The Center for Security Informatics (CSI) is dedicated to research, education and outreach. Much of the work that is done on a day-to-day basis can lean very strongly to one of those three categories while having an effect on the other two. At the same time, there are projects that directly involve all three goals in one package. This project is one of those: hacking a voting machine.
Voting machine security is one of the utmost concerns in the worlds of computing and politics. Making sure the tools that we use to elect office holders are free from potential tampering is a very serious matter and one that has received a tremendous amount of research and public attention in the last decade. As concerns have been brought to the fore, researchers have brought their concerns to the industry to make both technical and procedural improvements in their use.
For these reasons, when our center was able to get our hands on a used voting machine, we were very excited to put it to use as a learning tool for our summer interns and researchers to use as a tool to learn the basics of security penetration testing. Within a couple of hours we had immediate results that were very interesting and educational.
Our threat model was this: Given that a voter has 3-5 minutes alone with a voting machine, what could a user do to interfere with valid election results? Could they gain access to the machine’s critical components? Could they read/copy/modify data? Could they create a denial of service attack?
Given these questions, our first point of interest was the lock, which was easily pickable (see the video below). This gave us access to the USB flash drive, paper tape, and modem port. We were, frankly, surprised at how easily the lock was defeated.
That took about two seconds!
With physical access to the machine, we were able to pull the USB drive and do analysis on the empty drive inside. Since the drive had not been wiped, we had a good opportunity to run a variety of data recovery packages across the drive. Some students come to the program with skills in either of these areas, but most do not, so the practical experience was a superb opportunity. In this case, these provided us with significant data to work with, including both a voting database and a large binary file.
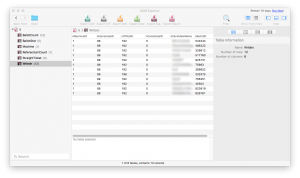
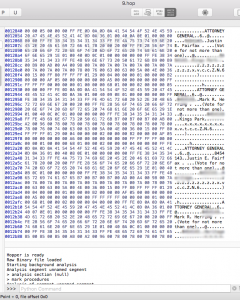
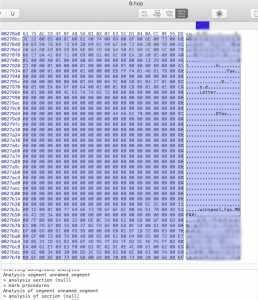
Accessing the database was done through a simple Microsoft Access database reading program. The database included write in data, names, tallies and additional information (blurred in the pictures for privacy concerns). It was not immediately clear if the database information was for full vote tallying or if it was a part of an audit function – although the candidates listed were valid for the 2012 election. Additionally, it did appear that the data would be modifiable. The binary file presented us with a learning opportunity for running a disassembler and looking at hexadecimal data. In a very cursory investigation, we found the names of candidates, related fields and what appeared to be the software used by the modem/fax to send data. This is where our first lab ended.
So what did our group learn and what steps do they plan to take next in this kind of research?
- Threat Model Thinking: What are the avenues of attack? What is possible? What would a creative/dedicated attacker do?
- Penetration Testing: Limiting ourselves to quick physical access attacks, we were able to put lock-picking practice to use in picking the unit’s locks quickly and effectively.
- Hardware Weakness Analysis: Once opened, the attacker has access to the USB drive, paper tape and modem. What do these provide to an attacker?
- Data Forensics: The blank USB provides an opportunity for data recovery analysis and identifying the usability of the resultant data.
- Binary Analysis: Students have to recognize that the output is a binary and then learn the use of binary disassembly tools to look at the data and harvest data, function or even look at changing the binary file for malicious use.
- Continued Avenues Of Study: Knowing what we discovered in just a couple of hours, what should come next? Students need to consider what additions, removals, and modifications we need to make for our threat model. Should we continue to focus on just the quick hacks that can be done on the machine in the timeframe that a voter would have at the booth, or do we want to tear the machine down further? Each of these choices is important to our next steps.
Some of the learning opportunities that the IoT House and the Center on Security informatics bring to students are very practical. We look at actual devices as tools for learning and combine those with a creative mindset that looks into what can be done given device misuse. Like a class in the “dark arts,” we combine the intent to do good, and the mind that can imagine evil and research carefully into what holes there are in our critical technological systems. Then we take that information and do the outreach to industry and schools to build up a more secure future.
This learning tool will be well used by the center, not only in direct, hands-on research, but also in its use with educational outreach to events like Indiana Women In Computing, our High School Capture the Flag/Hackathon outreach events, or any of our other outreach events. We expect not only to help create more secure voting machines as a long term result, but a stronger cyber security body of students and professionals working throughout industry, academia and industry as a direct result.